A 3rd party library is a collection of code provided by an external vendor. In software development is the use of 3rd party libraries normal and widespread. There is a large number of libraries available for different purposes. The use of consolidated code, that these libraries contain, can simplify and accelerate the software development. In the context of VCF Automation the PowerShell, Node.js and Python runtime environment make it very easy to create and use packages with these kind of libraries. However, I have not been able to find any sources on the aspect of using 3rd party libraries with the JavaScript runtime environment, which bases on the Rhino Engine. Reason enough to take a look at it
Use JavaScript 3rd Party Libraries,
with LINQ as an Example
As an example I take the JavaScript library LINQ by Mihai Ciuraru. This is a JavaScript implementation of the .NET LINQ library. It contains all the methods plus a few additions, it is written in pure JavaScript with no dependencies and it is under the MIT license.
LINQ (Language-Integrated Query) itself defines a set of standard query operators that allow e.g. filter or projection operations to be expressed in a direct but declarative way. A very good approach to create powerful and at the same time more understandable queries.
Some limitations have to be accepted, nothing that sets the world on fire but good to know:
- Rhino supports arrow functions since version 1.7.8, the older version supports only regular functions. The version 1.7R4 is used in VCF Automation until release 8.16.2. This is important to know because many examples are coded with arrow functions.
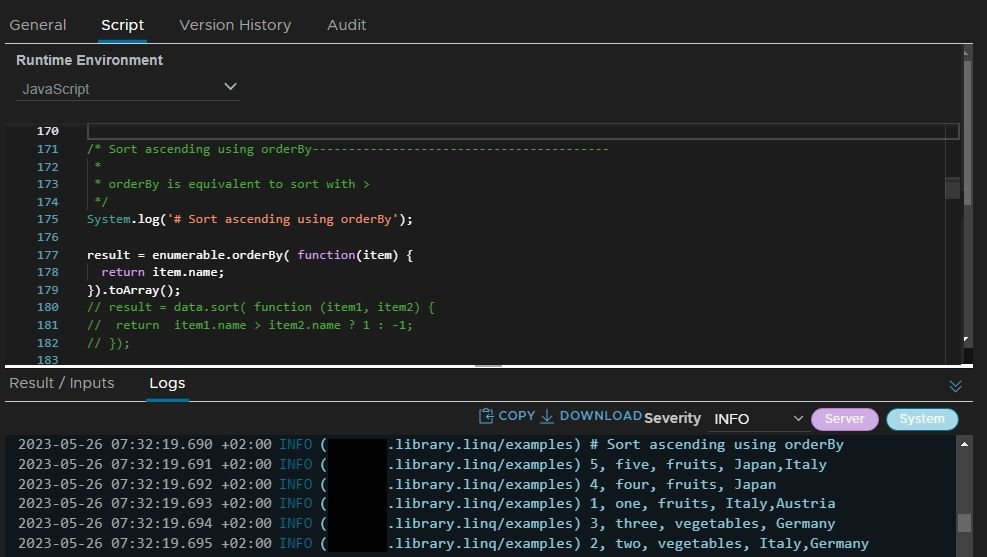
- The LINQ library supports lambda syntax (dot notation) and not query expression.
- Rhino does not support variable declaration with let and const, therefore these must be replaced by var.
- Rhino does not support export declaration, therefore the line export default Enumerable; at the end must be deleted.
- Rhino has no console window, therefore it is recommended to replace the code sequences if (typeof console !== Types.Undefined) { console.log(...); } with System.log(...).
| LINQ | JS |
|---|---|
result = data.orderBy(
function(item) {
return item.name;
}
); |
result = data.sort(
function (item1, item2) {
return item1.name > item2.name ? 1 : -1;
}
); |
result = data.orderByDescending(
function(item) {
return item.name;
}
); |
result = data.sort(
function (item1, item2) {
return item1.name < item2.name ? 1 : -1;
}
); |
result = data.sum(
function(item) {
return item.id;
}
); |
result = data.map(
function(item) { return item.id; }
).reduce(
function(item1, item2) { return item1 + item2 }
); |
You can find more examples in the LINQ JavaScript test file in my fork of the project.